Royal ransomware or Royal for short, was first observed in September 2022. Once infected, the requested demand for payment has been seen to range anywhere from $250,000 U.S. Dollars (USD) to over $2 million USD. The Ransomware appears to be targeting Healthcare Sector
Royal is a newer ransomware, and less is known about the malware and operators than others. Additionally, on previous Royal compromises that have impacted the Healthcare Sector, they have primarily appeared to be focused on organizations in the United States.
Royal is an operation that appears to consist of experienced actors from other groups, as there have been observed elements from previous ransomware operations. While most of the known ransomware operators have performed Ransomware-as-a-Service. Just to be clear Royal Ransomware is akin to a brand. They make the Software
Royal appears to be a private group without any affiliates while maintaining financial motivation as their goal. The group does claim to steal data for double-extortion attacks, where they will also exfiltrate sensitive data.
Multiple actors have been spreading Royal ransomware, but in a report from Microsoft, it is also being distributed by DEV-0569. The group has been delivering the malware with human-operated attacks and has displayed innovation in their methods by using new techniques, evasion tactics, and post-compromise payloads
DEV-0569 has been observed embedding malicious google ad links, known as “malvertising”, phishing emails, fake forums, and blog comments. In addition, Microsoft researchers have identified changes in their delivery method to start using malvertising in Google ads, utilizing an organization’s contact forum that can bypass email protections, and placing malicious installer files on legitimate looking software sites and repositories.
Once a network has been compromised, they will perform activities commonly seen from other operations, including deploying Cobalt Strike for persistence, harvesting credentials, and moving laterally through a system until they ultimately encrypt the files.
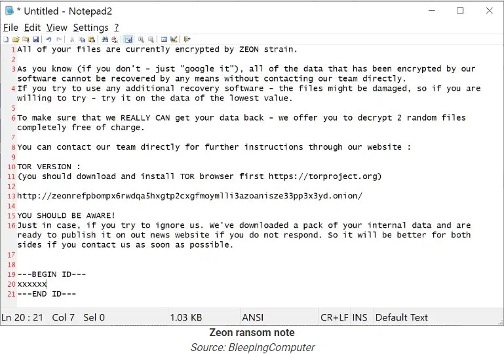
The ransom notes appear in a README.TXT as follows:
The Royal Ransomware can be identified by the following:
- Uses a 64-bit executable that is written in C++ and targets window systems
- Deletes and Copies all Volume Shadow Copies, which provides a point-in-time copy of a file
- Encrypts the network shares that are found on the local network and the local
- Uses AES algorithm, with the key and IV being encrypted in the hard-coded RSA public key
- Changes the extension of the files to ‘.royal’.
Outside of the techniques addressed in this report, HC3 continues to see the following attack vectors frequently associated with ransomware:
- Phishing
- Remote Desktop Protocol (RDP) compromises and credential abuse
- Compromises of exploited vulnerabilities, such as VPN servers
- Compromises in other known vulnerabilities