The Cyber Security and Infrastructure Security Agency (CISA) has come to the rescue for those affected by a Recent Ransomware Virus called ESXiArgs.
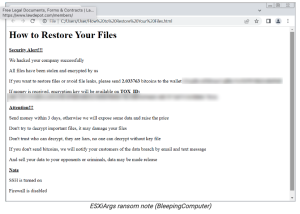
CISA has released yesterday a recovery script for organizations that have fallen victim to ESXiArgs ransomware. The ESXiArgs ransomware encrypts configuration files on vulnerable ESXi servers, potentially rendering virtual machines (VMs) unusable.
The ESXiArgs is a that ransomware encrypts files with the .vmxf, .vmx, .vmdk, .vmsd, and .nvram extensions on compromised ESXi servers and creates a .args file for each encrypted document with metadata (likely needed for decryption).
VMware warned customers on Monday to install the latest security updates and disable the OpenSLP service targeted in a large-scale campaign of ransomware attacks against Internet-exposed and vulnerable ESXi servers.
The company added that the attackers aren’t exploiting a zero-day vulnerability and that this service is disabled by default in ESXi software releases issued since 2021.
The threat actors also target products that are “significantly out-of-date” or have already reached their End of General Support (EOGS), according to VMware.
CISA recommends organizations impacted by ESXiArgs evaluate the script and guidance provided in the accompanying README file to determine if it is fit for attempting to recover access to files in their environment.
Organizations can access the recovery script here: https://github.com/cisagov/ESXiArgs-Recover
0