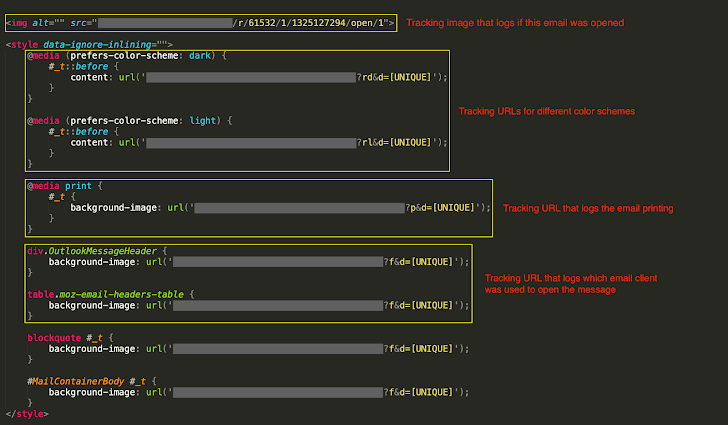
Recent research from Cisco Talos has revealed that cybercriminals are exploiting Cascading Style Sheets (CSS) to bypass email security filters and track user interactions. CSS, a fundamental tool for web design, is being manipulated to conceal malicious content within emails, making it more difficult for spam filters and detection engines to identify phishing attempts.
One of the primary techniques observed involves the use of CSS properties such as text-indent and opacity to hide sections of text, rendering them invisible to email recipients while still allowing attackers to evade detection. Additionally, threat actors are leveraging the @media CSS at-rule to track user behavior by collecting data on recipients’ screen size, resolution, language preferences, and email client settings. This form of fingerprinting can provide attackers with valuable intelligence for further targeted attacks.
These findings build upon previous research into hidden text salting, a technique that inserts irrelevant but invisible content within emails to confuse security filters. By abusing legitimate HTML and CSS features, attackers can manipulate how email content is rendered, increasing the likelihood of evading detection. In some cases, these techniques are used to redirect recipients to phishing websites, further increasing the risk of credential theft and malware infections.
The implications of this technique are significant, as it enables attackers to circumvent traditional spam and phishing detection mechanisms while gathering intelligence on users’ environments. To mitigate these risks, organizations and individuals should implement advanced email filtering mechanisms capable of detecting hidden text and CSS-based obfuscation. Additionally, using email privacy proxies can help prevent tracking attempts, reducing the ability of threat actors to monitor user actions.
As cybercriminals continue to refine their methods, it is essential for organizations and security teams to stay informed and adapt their defenses accordingly. Awareness of these evolving threats, combined with proactive security measures, is crucial to protecting sensitive data and maintaining email security.