So, a lot of organizations are moving to Microsoft Office 365 for a variety of reasons, one of those being ease of operation and deployment. Secondarily, Microsoft Office 365 maybe more secure than self-hosted email platforms.
IS YOUR OFFICE 365 SECURE?
But… Microsoft Office 365 Security is often a mis-overlooked application mainly because we just assume it is safe.
Microsoft has published documentation with the Required Security Tasks to make it Secure. We have included the links as well. If you need more information, please contact Topgallant Partners on our contact form. Here are the Steps. hope it helps…
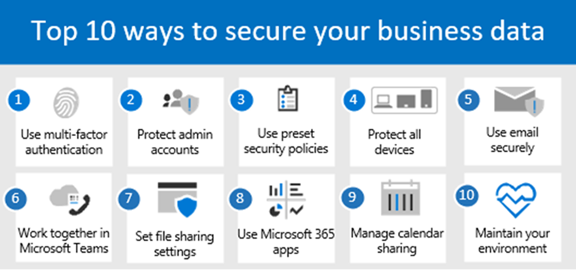
Required Security Tasks Detail
| Step | Task | Description |
| 1 | Use multi-factor authentication. | Multi-factor authentication (MFA), also known as two-step verification, requires people to use a code or authentication app on their phone to sign into Microsoft 365, and is a critical first step to protecting your business data. Using MFA can prevent hackers from taking over if they know your password.
|
| 2 | Protect your administrator accounts. | Administrator accounts (also called admins) have elevated privileges, making these accounts more susceptible to cyberattacks. You’ll need to set up and manage the right number of admin and user accounts for your business. We also recommend adhering to the information security principle of least privilege, which means that users and applications should be granted access only to the data and operations they require to perform their jobs.
|
| 3 | Use preset security policies. | Your subscription includes preset security policies that use recommended settings for anti-spam, anti-malware, and anti-phishing protection.
|
| 4 | Protect all devices. | Every device is a possible attack avenue into your network and must be configured properly, even those devices that are personally owned but used for work.
See the following articles: |
| 5 | Train everyone on email best practices. | Email can contain malicious attacks cloaked as harmless communications. Email systems are especially vulnerable, because email is handled by everyone in the organization, and safety relies on humans making consistently good decisions with those communications. Train everyone to know what to watch for spam or junk mail, phishing attempts, spoofing, and malware in their email.
|
| 6 | Use Microsoft Teams for collaboration and sharing. | The best way to collaborate and share securely is to use Microsoft Teams. With Microsoft Teams, all your files and communications are in a protected environment and aren’t being stored in unsafe ways outside of it.
See the following articles: |
| 7 | Set sharing settings for SharePoint and OneDrive files and folders. | Your default sharing levels for SharePoint and OneDrive might be set to a more permissive level than you should use. We recommend reviewing and if necessary, changing the default settings to better protect your business. Grant people only the access they need to do their jobs.
See Set sharing settings for SharePoint and OneDrive files and folders. |
| 8 | Use Microsoft 365 Apps on devices. | Outlook and Microsoft 365 Apps (also referred to as Office apps) enable people to work productively and more securely across devices. Whether you’re using the web or desktop version of an app, you can start a document on one device, and pick it up later on another device. Instead of sending files as email attachments, you can share links to documents that are stored in SharePoint or OneDrive.
See the following articles: |
| 9 | Manage calendar sharing for your business. | You can help people in your organization share their calendars appropriately for better collaboration. You can manage what level of detail they can share, such as by limiting the details that are shared to free/busy times only.
|
| 10 | Maintain your environment. | After your initial setup and configuration of Microsoft 365 for business is complete, your organization needs a maintenance and operations plan. As employees come and go, you’ll need to add or remove users, reset passwords, and maybe even reset devices to factory settings. You’ll also want to make sure people have only the access they need to do their jobs.
|

