
London, UK – The Department of Justice joined the United Kingdom and international law enforcement partners in London today to announce the disruption of the LockBit ransomware group, one of the most active ransomware groups in the world that has targeted over 2,000 victims, received more than $120 million in ransom payments, and made ransom demands totaling hundreds of millions of dollars.
The Justice Department has unsealed an indictment obtained in the District of New Jersey charging Russian nationals Artur Sungatov and Ivan Kondratyev, also known as Bassterlord, with deploying LockBit against numerous victims throughout the United States, including businesses nationwide in the manufacturing and other industries, as well as victims around the world in the semiconductor and other industries. Additional criminal charges against Kondratyev were also unsealed in the Northern District of California related to his deployment in 2020 of ransomware against a victim located in California.
The LockBit ransomware variant, like other major ransomware variants, operates in the “ransomware-as-a-service” (RaaS) model, in which administrators, also called developers, design the ransomware, recruit other members — called affiliates — to deploy it, and maintain an online software dashboard called a “control panel” to provide the affiliates with the tools necessary to deploy LockBit.
Affiliates, in turn, identify and unlawfully access vulnerable computer systems, sometimes through their own hacking or at other times by purchasing stolen access credentials from others. Using the control panel operated by the developers. The affiliates then deploy LockBit within the victim computer system, allowing them to encrypt and steal data for which a ransom is demanded to decrypt or avoid publication on a public website maintained by the LockBit developers, often called a data leak site.
Sungatov allegedly deployed LockBit ransomware against manufacturing, logistics, insurance, and other companies located in Minnesota, Indiana, Puerto Rico, Wisconsin, Florida, and New Mexico. Additionally, as early as August 2021, Kondratyev similarly began to allegedly deploy LockBit against multiple victims.
Kondratyev, operating under the online alias “Bassterlord,” allegedly deployed LockBit against municipal and private targets in Oregon, Puerto Rico, and New York, as well as additional targets located in Singapore, Taiwan, and Lebanon.
Both Sungatov and Kondratyev are alleged to have joined in the global LockBit conspiracy, also alleged to have included Russian nationals Mikhail Pavlovich Matveev and Mikhail Vasiliev, as well as other LockBit members, to develop and deploy LockBit ransomware and to extort payments from victim corporations.
The U.K. National Crime Agency’s (NCA) Cyber Division, working in cooperation with the Justice Department, Federal Bureau of Investigation (FBI), and other international law partners disrupted LockBit’s operations by seizing numerous public-facing websites used by LockBit to connect to the organization’s infrastructure and seizing control of servers used by LockBit administrators, thereby disrupting the ability of LockBit actors to attack and encrypt networks and extort victims by threatening to publish stolen data.
Additionally, the NCA, in cooperation with the FBI and international law enforcement partners, has developed decryption capabilities that may enable hundreds of victims around the world to restore systems encrypted using the LockBit ransomware variant. Beginning today, victims targeted by this malware are encouraged to contact the FBI at https://lockbitvictims.ic3.gov/ to enable law enforcement to determine whether affected systems can be successfully decrypted.
0

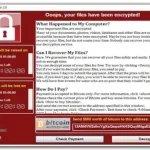
That’s a win for the good guys.