Google released its latest issue of Mandiant’s Cyber Snapshot Report. This Issue (Number 7) includes five cyber defense topics and expert guidance. According to Mandiant there is a key cyber necessity to “reduce the growing risk of insider threats with penetration testing”.
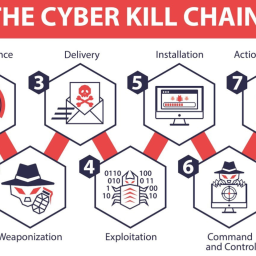
According to Google, external attacks often grab headlines, but the danger lurking within is that most organizations often overlook is the insider threat, which can inflict catastrophic damage. While traditional penetration testing is a good start, it’s not enough. Organizations need to go beyond the perimeter and take swift, decisive action against insider threats.
An insider threat penetration test offers the tools and insights necessary to do just that, enabling companies to stay one step ahead of potential insider risks, safeguard their most valuable assets, and create a security-aware culture that enables employees to contribute in being a part of the first line of defense against insider threats.
The significance of insider attacks in today’s complex business environment cannot be overstated. The frequency of these incidents has increased significantly over the last 12 months:
76% of organizations have reported insider attacks in 2024, up from 66% in 2019
—and the average cost per incident has reached millions of dollars.
Insiders possess legitimate credentials and understand internal systems, making their potential attacks more damaging than one might imagine.
To combat this growing risk, security conscious organizations are turning to insider threat penetration testing as a crucial component of their security strategy.
The Primary Objective of Internal Penetration Testing
The purpose of threat penetration testing is to uncover and address vulnerabilities that could be exploited by individuals with insider access to your organization. The scope of threat penetration testing involves:
- Identifying gaps in access controls and privileges
- Testing the effectiveness of data loss prevention measures
- Evaluating insider threat detection and response capabilities
- Assessing the potential impact of successful insider attacks
Other Topics in the report include:
- Assess and protect your web-based LLM applications
- Apply a best-practice plan to migrate from a legacy to leading-edge SIEM platform
- Deploy a deception strategy to defend against attackers
- Adopt proactive security measures to harden cloud-based environments
- Stay one step ahead with your cyber defense – get the report today.
- The Defender’s Advantage Cyber Snapshot report provides insights into cyber defense topics of growing importance based on Mandiant frontline observations and real-world experiences.
The entire report can be accessed at https://cloud.google.com/security/resources/cyber-snapshot-reports
If you need an internal penetration test or for more information please contact us at https://topgallant-partners.com
1image sources
- Screenshot 2024-08-22 at 10.27.17 AM: Topgallant Partners ©2025