This is the third video that will demonstrate how to use the Saint Penetration Tool and Windows Command Line to Cover Your Tracks by deleting Event Viewer files and deleting the administrative user that you created.
0Related Posts
September 19, 2012 Well, It looks like the HIPAA Enforcement Boys and Girls are getting serious. Mass Eye and Ear…
0Two Days ago, CISA released an Industrial Controls Systems Advisory (ICSA) detailing six vulnerabilities that were discovered in MiCODUS MV720 Global Positioning System (GPS) Tracker
0
Topgallant Partners was recently Certified by New York as a New York State Certified Service-Disabled Veteran Owned Business. Topgallant Received the news in April. The news was received in a letter written by the Executive Director for Division of Service-Disabled Veterans’ Business Development, Kenneth E. Williams.
1
Healthcare spending in the U.S. — which is the highest among developed countries — accounts for 18 percent of the…
0
Microsoft Zero Day Vulnerability/Exploit Follina Found A Zero-Day Vulnerability/Exploit “Follina” has been found in Microsoft Office and Microsoft Windows…
0
Introduction: Ransomware has become a prevalent and damaging threat in the world of cybersecurity. This malicious software aims to encrypt…
1
CISA assesses that the United States and European nations may experience disruptive and defacement attacks against websites in an attempt…
0
Washington, DC – Today, CISA, the Federal Bureau of Investigation (FBI), Europol’s European Cybercrime Centre (EC3), and the Netherlands’ National…
0
HealthEC LLC a New Jersey based health technology company reported a data breach that impacted nearly 4.5 million patients across…
0
Have you ever wondered what a Salted Hash was? Well, here is the Cliff Notes’ Version Hashing is a function…
0
CONCORD – A Derry man pleaded guilty in federal court in Concord to passport fraud and wire fraud in connection…
0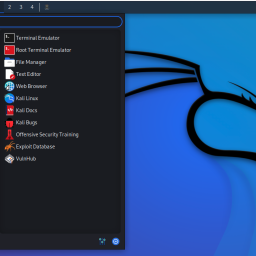
Seemingly Benign Programs used for Hacking Hackers use seemingly benign programs for Nefarious Purposes. Hackers manipulate and repurpose software and…
1
The Justice Department announced today a disruption campaign against the Blackcat ransomware group — also known as ALPHV or Noberus…
0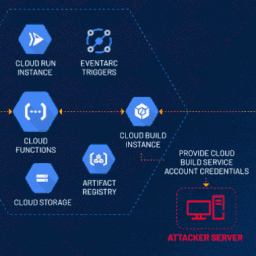
In the constantly evolving landscape of cloud computing, ensuring robust security measures is paramount. Recently, cybersecurity researchers have identified a…
0
The Cyber Security and Infrastructure Security Agency (CISA) has come to the rescue for those affected by a Recent Ransomware…
0
