This is the third video that will demonstrate how to use the Saint Penetration Tool and Windows Command Line to Cover Your Tracks by deleting Event Viewer files and deleting the administrative user that you created.
0His expertise is in Security Program Design, Security Risk Analysis and Assessment and Cyber Security Testing to include Penetration Testing, Vulnerability Testing, Social Engineering, Phishing, Wi-Fi Exploitations, Password Cracking, Man-in-the Middle Attacks and Web Application Hacking.
He has a M.A. in Computer Resources Management from Webster University and a B.A. in Journalism from Purdue University. He is also a terrible golfer.
Related Posts

“The incident may have affected approximately 500,000…
1
May 2023 Newsletter Tim Cook Said Recently “In The World of Cybersecurity The Last Thing You Want Is To Have…
1
CISA assesses that the United States and European nations may experience disruptive and defacement attacks against websites in an attempt…
1
VMware has released fixes for ten vulnerabilities, including CVE-2022-31656 which is an authentication bypass vulnerability affecting VMware Products. VMware considers these updates critical and advises to patch or mitigate immediately. There is an indication that this vulnerability may soon be leveraged by attackers.
0
The Cyber Security and Infrastructure Security Agency (CISA) has come to the rescue for those affected by a Recent Ransomware…
0
Strengthening Industrial Control Systems Cybersecurity: Learning from the Bosch Torque Wrench Breach The recent cyber breach involving Bosch’s torque wrench…
1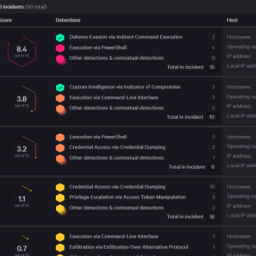
Introduction In the quest to strengthen cybersecurity defenses, organizations have turned to various solutions such as SIEM, XDR/MDR, and SOAR….
6September 19, 2012 Well, It looks like the HIPAA Enforcement Boys and Girls are getting serious. Mass Eye and Ear…
0
HealthEC LLC a New Jersey based health technology company reported a data breach that impacted nearly 4.5 million patients across…
0
Have you ever wondered what a Salted Hash was? Well, here is the Cliff Notes’ Version Hashing is a function…
1
The Justice Department announced today a disruption campaign against the Blackcat ransomware group — also known as ALPHV or Noberus…
1Two Days ago, CISA released an Industrial Controls Systems Advisory (ICSA) detailing six vulnerabilities that were discovered in MiCODUS MV720 Global Positioning System (GPS) Tracker
1
CONCORD – A Derry man pleaded guilty in federal court in Concord to passport fraud and wire fraud in connection…
0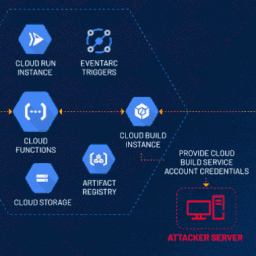
In the constantly evolving landscape of cloud computing, ensuring robust security measures is paramount. Recently, cybersecurity researchers have identified a…
0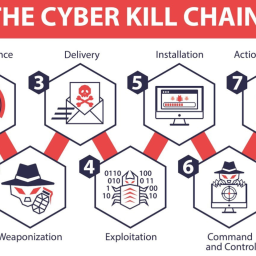
What is the Mitre ATT&CK Framework? The Mitre ATT&CK Framework describes the techniques, tactics and procedures that hackers use to…
2
