What is the Mitre ATT&CK Framework?
The Mitre ATT&CK Framework describes the techniques, tactics and procedures that hackers use to carry out cyberattacks. An important concept from the Mitre ATT&CK framework is the “Kill Chain,” which is a model that describes stages or phases that an attacker typically follows when conducting a cyberattack. This model helps organizations understand and defend against cyber threats by listing them as steps below.
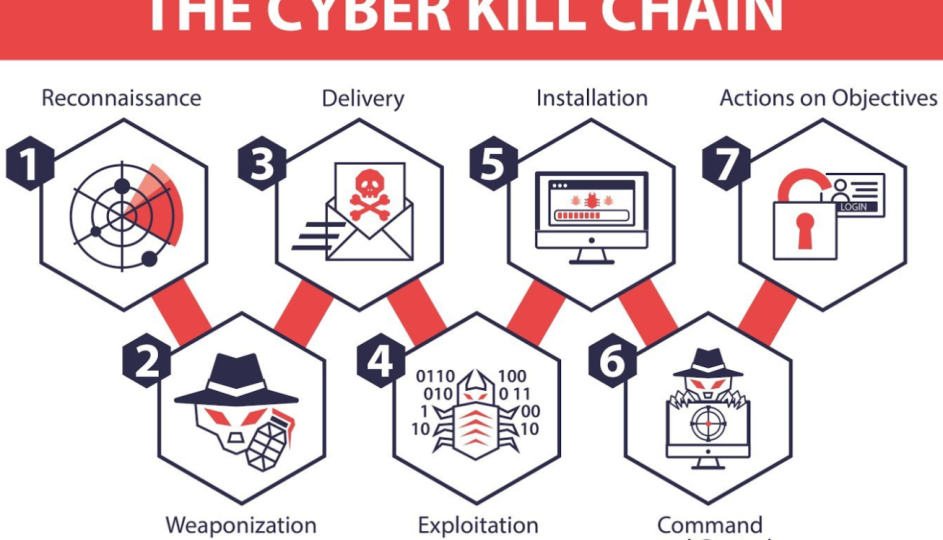
Kill Chain model
There are seven steps and I included briefly what is “done” during each step. Note that although it is listed as a step-by-step model it is not linear. Attackers can move back and forth between stages.
- Reconnaissance– Attackers gather information about the target. They might use social media, websites, or public databases to understand the target environment, employees, and their systems.
- Weaponization– attackers create a malicious payload, like a virus or worm. They use tools and techniques to package the payload in a way that can exploit vulnerabilities in the target’s systems.
- Delivery– Attackers send the weaponized bundle to the victim. This could be through phishing emails, malicious downloads, or other methods to ensure the target receives the malware.
- Exploitation– The malicious code gets executed on the victim’s system. This could be by tricking a user to click on something or by exploiting a software vulnerability.
- Installation– After exploitation, the malware installs itself to maintain persistence. This means it ensures it remains in the system even after reboots or attempts to remove it.
- Command and Control (C2)– The malware establishes a backdoor to the attacker, allowing remote control over the infected system. This way, attackers can issue commands, extract data, or further spread inside the network.
- Action on Objectives– This is the endgame. Having infiltrated the system, attackers now pursue their goals. This could be data theft, deploying ransomware, causing system disruption, or any other malicious intent.
While we can never fully eliminate cyber threats, however by understanding how attackers operate and the techniques they use, organizations can better prepare and defend against cyber-attacks. They can also better detect attacks and respond efficiently to mitigate risks, and impact of security incidents.
2