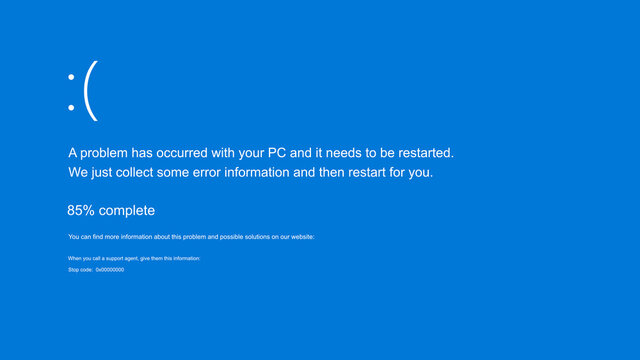
The Core Problem Devices utilizing Windows Client and Windows Server that automatically installed a CrowdStrike security update on Friday morning…
it security audit
Let’s unpack the symbiotic relationship between cybersecurity and video surveillance. In the fast-paced world of digital defense, understanding how these…
The NIST Cybersecurity Framework (CSF), developed by the National Institute of Standards and Technology, plays a pivotal role in bolstering…
Measuring Risk The definition of Risk is: risk = likelihood x impact. This formula is not abstract and makes sense….
IT Risk Assessment Benefits 1. Documents Due Diligence An IT Risk Assessment provides verification and validation of an organization’s adherence to…
Penetration Test vs. Vulnerability Assessment What I learned in the Sea Services (Marines) is that a ship can carry a…
The Payment Card Industry (PCI) Council has updated their guidance on penetration testing. The guidance provides specifics about misconceptions surrounding…
Town of Tewksbury MA Pays to get rid of Ransomware Infection. Here we go again. Looks like the Tewksbury Police…
The Federal Financial Institutions Examination Council (FFIEC) released statements on ways that financial institutions can identify and mitigate cyber attacks…
According to a statement issued by Premera Blue Cross, a hacker was able to gain unauthorized access to its Information…