May 2023 Newsletter
Tim Cook Said Recently “In The World of Cybersecurity The Last Thing You Want Is To Have a Target Painted On Your Back”
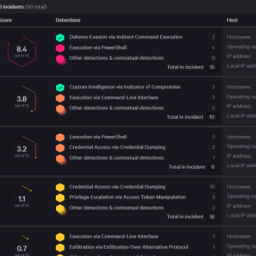
The Near Inevitability of Cybersecurity Breaches Calls for Greater Focus on Identification, Response and Recovery through Incident Recovery Preparedness
- According to The Cost of a Data Breach Report 86% of the participants said they had been breached more than once.
- 79% of Critical Infrastructure Organizations said they had not deployed a Zero Trust Architecture.
- 19% of breaches occurred due to business partner compromise.
- 45% of the breaches were cloud based.
- Average cost of a breached record $164.00
- Estimated time to identify a breach 200+ days.
- Source: IBM and Ponemon Group Breach Report
How to Reduce the Inevitability of a Cybersecurity Breach
- Document written IT Control cybersecurity policies, procedures, and plans.
- Perform a Cybersecurity Risk Assessment based on a framework like NIST CSF.
- Perform a Vulnerability Assessment or Penetration Test to identify vulnerabilities and exploits, patch all systems based on findings and re-test.
- Provide employee security training and awareness programs with reminders and testing.
- Adopt a Zero Trust Model to Prevent Unauthorized Access to Data.
- Protect sensitive data in cloud environments using policy and encryption.
- Invest in security orchestration, automation and response (SOAR) and EDR, MDR, and XDR to help improve detection and response times.
- Protect and monitor endpoints and remote employees.
Create and Test incident response plans and teams to increase training and awareness before a breach occurs.
- Increase IT spend it’s cheaper than a breach
- Invest in your IT people through advanced training and certifications.
- Deploy application aware firewalls.
- Penetration Test custom applications and databases during the development phase.
- Encrypt Data at rest and in transport.
- Deploy 2 factor authentication.
- Filter outgoing and inbound traffic.
- Perform Audits of Business Associate Agreements for Cybersecurity adherence.
- Turn off USB Ports.
- Turn off Data Jack Ports.
- Secure and Upgrade Data Centers and Wiring Closet Physical Security
- Perform Red Team exercises to enhance the effectiveness of IR teams by uncovering attack paths and techniques they might miss and identifying gaps in their detection and response capabilities.
- Test your Cloud Implementation. Amazon and Microsoft only protect their infrastructure and advise clients to perform testing that they allow.
Vigilance is Key:
Companies realize a lower probability of a breach when they use a cybersecurity risk framework to evaluate their cybersecurity posture. The reduced attack surface has fewer vulnerabilities resulting in less attack vectors making it more difficult and time consuming for a hacker to perform reconnaissance looking for a Exploit.
0