This is the third video that will demonstrate how to use the Saint Penetration Tool and Windows Command Line to Cover Your Tracks by deleting Event Viewer files and deleting the administrative user that you created.
0His expertise is in Security Program Design, Security Risk Analysis and Assessment and Cyber Security Testing to include Penetration Testing, Vulnerability Testing, Social Engineering, Phishing, Wi-Fi Exploitations, Password Cracking, Man-in-the Middle Attacks and Web Application Hacking.
He has a M.A. in Computer Resources Management from Webster University and a B.A. in Journalism from Purdue University. He is also a terrible golfer.
Related Posts

Have you ever wondered what a Salted Hash was? Well, here is the Cliff Notes’ Version Hashing is a function…
1Hi All, In my last Video Demo, I exploited the Default SNMP String on a Cisco Router and gained access…
0
Microsoft Zero Day Vulnerability/Exploit Follina Found A Zero-Day Vulnerability/Exploit “Follina” has been found in Microsoft Office and Microsoft Windows…
1
The Justice Department announced today a disruption campaign against the Blackcat ransomware group — also known as ALPHV or Noberus…
1
VMware has released fixes for ten vulnerabilities, including CVE-2022-31656 which is an authentication bypass vulnerability affecting VMware Products. VMware considers these updates critical and advises to patch or mitigate immediately. There is an indication that this vulnerability may soon be leveraged by attackers.
0
Washington, DC – Today, CISA, the Federal Bureau of Investigation (FBI), Europol’s European Cybercrime Centre (EC3), and the Netherlands’ National…
0
May 2023 Newsletter Tim Cook Said Recently “In The World of Cybersecurity The Last Thing You Want Is To Have…
1
In a universe (not so far away), where passwords like “123456” and “password” reigned supreme, our hero, NIST 800-63B, stepped…
3
HealthEC LLC a New Jersey based health technology company reported a data breach that impacted nearly 4.5 million patients across…
0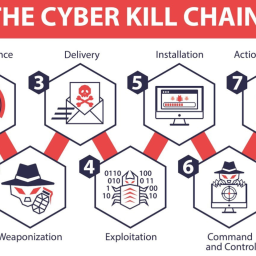
What is the Mitre ATT&CK Framework? The Mitre ATT&CK Framework describes the techniques, tactics and procedures that hackers use to…
2
The U.S. Department of Justice has indicted five individuals—including North Korean, Mexican, and U.S. nationals—for their role in a fraudulent…
1
Healthcare spending in the U.S. — which is the highest among developed countries — accounts for 18 percent of the…
1
“The incident may have affected approximately 500,000…
1
Seemingly Benign Programs used for Hacking Hackers use seemingly benign programs for Nefarious Purposes. Hackers manipulate and repurpose software and…
2
Strengthening Industrial Control Systems Cybersecurity: Learning from the Bosch Torque Wrench Breach The recent cyber breach involving Bosch’s torque wrench…
1
