Health and Human Services (HHS) proposes specific modifications to HIPAA Security Rule to Protect EPHI.
Vulnerability Assessment
We all know what is meant by Access Control. Pretty easy to figure out? There are all kinds of access…
Google released its latest issue of Mandiant’s Cyber Snapshot Report. This Issue (Number 7) includes five cyber defense topics and…
We cannot forget about Change Management in today’s crazy, dangerous and very much evolving digital frontier. I think all the…
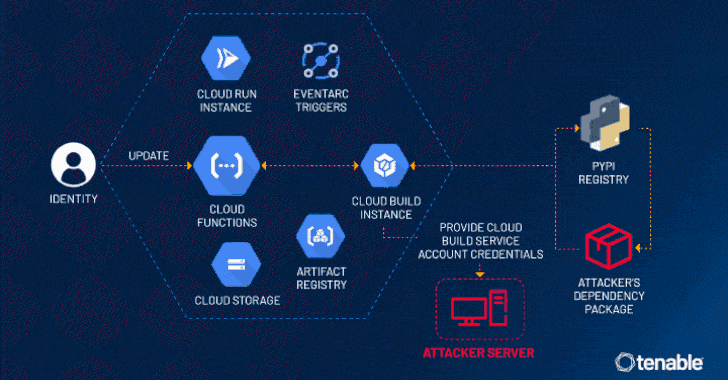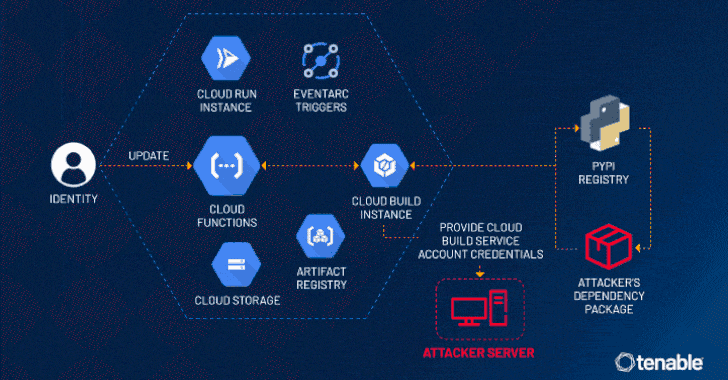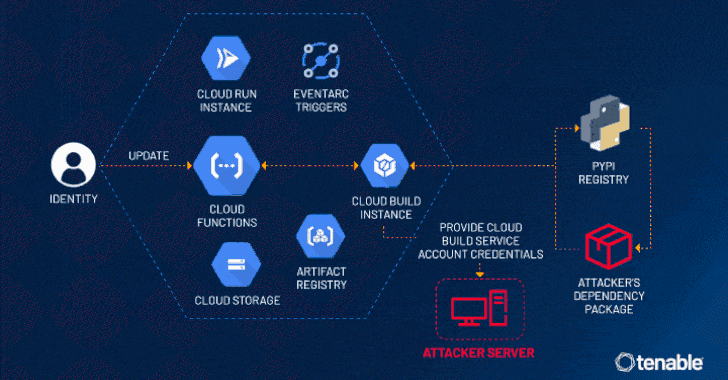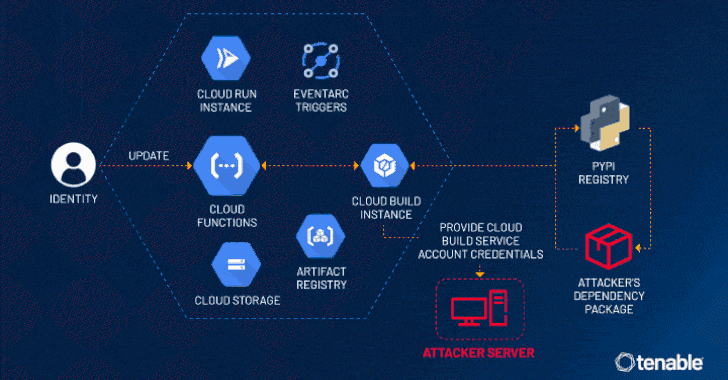
In the constantly evolving landscape of cloud computing, ensuring robust security measures is paramount. Recently, cybersecurity researchers have identified a…
Strengthening Industrial Control Systems Cybersecurity: Learning from the Bosch Torque Wrench Breach The recent cyber breach involving Bosch’s torque wrench…
Washington, DC – Today, CISA, the Federal Bureau of Investigation (FBI), Europol’s European Cybercrime Centre (EC3), and the Netherlands’ National…
CONCORD – A Derry man pleaded guilty in federal court in Concord to passport fraud and wire fraud in connection…
The NIST Cybersecurity Framework (CSF), developed by the National Institute of Standards and Technology, plays a pivotal role in bolstering…
In the ever-evolving landscape of wireless networking, security is a paramount concern. With the increasing prevalence of smart devices, IoT…